
CMMC Compliance
The requirements for CMMC compliance have undergone significant changes in the past year. With further changes planned, we look at the current CMMC 2.0 compliance requirements for businesses in the Defense Industrial Base and the options for those who have not yet met the requirements.
In November 2021, the Office of the Under Secretary of Defense for Acquisition and Sustainment announced significant changes to the Cybersecurity Maturity Model Certification (CMMC) framework in order to simplify the framework and provide “additional clarity on cybersecurity regulatory, policy, and contracting requirements”.
The “strategic direction” announcement was yet another change in direction for the hundreds of thousands of businesses in the Department of Defense supply chain (also known as the Defense Industrial Base) that research, design, manufacture, deliver, and maintain systems, weapons, and components for the Department of Defense.
Since the start of the Century, contractors supplying goods and services to the Department of Defense have had to comply with variations of the Federal Acquisition Regulation, the Federal Information Processing Standards (FIPS), the Federal Information Security Management Act (FISMA), FedRAMP, the Defense Federal Acquisition Regulation Supplemental (DFARS), and NIST SP 800–171.
Due to the variety of frequently-changing regulations, compliance with the requirements was low. One source reported that only 60% of contractors in the Defense Industrial Base complied with the requirements – raising concerns about the security of military data. The low compliance rate prompted the Department of Defense to review its acquisition requirements and release CMMC 1.0.
Why CMMC 1.0 Didn´t Work
When CMMC 1.0 was released in 2020, its five-level framework was scheduled to be rolled out over five-years. However, one of the challenges of complying with CMMC 1.0 was that every contractor in the Defense Industrial Base had to undergo a third-party audit during the roll-out period even though the CMMC requirements lacked “sufficient clarity and predictability in key areas”.
In addition, at the time CMMC 1.0 was due to come into effect, the CMMC Accreditation Body had not yet appointed or trained the Certified Third Party Assessment Organizations (C-3PAOs) responsible conducting the audits nor revealed the process by which contractors would be certified as CMMC compliant. The situation was not helped by the outbreak of the COVID-19 pandemic.
Due to the issues and the ongoing pandemic, the effective date of CMMC 1.0 was pushed back from June 2020 to September 2020 and then delayed indefinitely. In December 2020, a pilot scheme was announced for seven acquisition contracts which would require applicants to have C-3PAO certification. All other contracts would revery to the previous DFARS requirements.
CMMC 2.0 Launched with Significant Changes
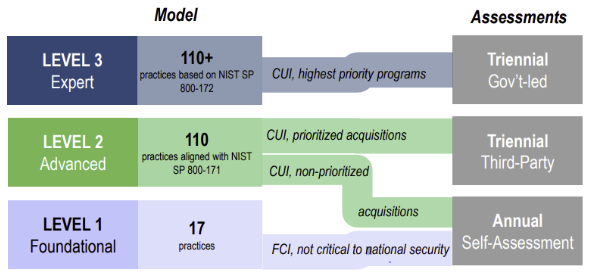
The “strategic direction” announcement of November 2021 significantly changed the CMMC compliance requirements. The five-level framework was reduced to three levels, and rather than all contractors having to undergo audits to become C-3PAO certified, only those with access to Controlled Unclassified Information (CUI) will need to meet this requirement.
| CMMC 2.0 Framework | Requirements |
|---|---|
| Level 1 – Foundation. For companies with access to Federal Contract Information (FCI) that requires protection, but that is not critical to national security. | Contractors and subcontractors will be required to comply with 48 CFR 52.204-21 . |
| Level 2 – Advanced. For companies with access to Controlled Unclassified Information (CUI) that – although not classified – requires protection from unauthorized access and disclosure. | Contractors and subcontractors will be required to comply with NIST SP 800-171 Revision 2 |
| Level 3 – Expert. This level is reserved for companies with access to CUI contracted to work on high priority programs. Note: The requirements for this Level are still being finalized. | Contractors and subcontractors will be required to comply with NIST SP 800-171 Revision 2 and a yet-to-be-determined subset of NIST SP 800-172. |
Although the requirements for Level 3 have not yet been finalized, and there are still issues with appointing and training C-3PAOs, the roll-out is going ahead with provisions in place to allow contractors to apply for DoD contracts even if they have not yet been audited for CMMC compliance (when required) or achieved the required level of certification.
These provisions allow contractors that do not yet meet the criteria for Level 1 contracts to submit a time-limited Plan of Actions and Milestones (POA&M), while contractors that that do not yet meet the criteria for Level 2 contracts can apply for time-limited waivers if they have already obtained FedRAMP or FIPS 140 certification. Waivers will be granted on a case-by-case basis.
The Requirements for CMMC Compliance
As they stand at present, the requirements for CMMC compliance do not look that complicated. The Level 1 requirements in 48 CFR 52.204-21 are no more than any business should already have implemented to protect corporate data and consist of:
- Access Controls
- Mechanisms for Identification and Authentication
- Safeguards for Media Protection
- Safeguards for Physical Protection
- System and Communications Protection
- System and Information Integrity
To achieve Level 2 CMMC compliance, businesses will have to implement additional best practices to the requirements for Level 1 and comply with the standards of NIST SP 800-171 r2 – which have more documentation requirements than Level 1. Areas of Level 2 compliance include:
- Awareness and Training
- Audit and Accountability
- Configuration Management
- Incident Response
- System Maintenance
- Personnel Security
- Risk Assessments
- Security Assessments
Until it has been decided which subset(s) of NIST SP 800-172 will be included in the Level 3 requirements, the Department of Defense is not requesting Level 3 CMMC 2.0 compliance for new contracts. It is also important to note that Level 1 and Level 2 CMMC requirements only apply to domestic contractors. The requirements for overseas contractors – and how overseas contractors will be audited for CMMC compliance – are also still to be decided.
How CMMC Compliance will be Certified
As mentioned above, rather than all contractors having to undergo audits to become C-3PAO certified, only those with access to Controlled Unclassified Information (CUI) will need to meet this requirement. This means that contractors applying for Level 1 contracts only have to self-asses CMMC compliance and submit an affirmation that the business meets 48 CFR 52.204-21.
As CMMC is rolled out, an increasing number of Level 2 contracts will require C-3PAO certification that the business complies with NIST SP 800-171 r2. Once the initial certification is completed, re-certification will be required every three years for “prioritized acquisitions”, while an affirmation of self-assessment (as with Level 1) will be required for “non-prioritized” acquisitions.
When the requirements for Level 3 CMMC compliance are announced, the Department of Defense will be directly responsibility for certifying companies applying for Level 3 contracts and auditing their ongoing compliance every three years. The DoD has also announced that, at some point in the future, self-assessments and will need to be registered in the Supplier Performance Risk System.
CMMC Compliance FAQs
Where can I find further information about what is included in Level 1 and Level 2 CMMC assessments?
The Office of the Under Secretary of Defense for Acquisition and Sustainment has an online documentation page from which you can download a CMMC Level 1 Self-Assessment Guide and a CMMC Level 2 Assessment Guide. These two guides explain the criteria for each assessment level and suggest ways in which companies can meet the requirements.
When might the requirements for CMMC Level 3 be announced?
At present, the next CMMC Interim Rule is forecast for publication in March 2023. It is not known yet whether this will include the requirements for CMMC Level 3 or address other outstanding issues such as how companies outside the United States can become certified as CMMC compliant.
If our company achieves Level 2 CMMC compliance, do any subcontractors we use also have to be Level 2 CMMC compliant?
This depends on what information is shared with or disclosed to the subcontractor. If your company shares or discloses CUI, the subcontractor(s) will have to be Level 2 CMMC compliant. If your company shares or discloses FCI, the subcontractor will have to be Level 1 CMMC compliant. If you company does not share or disclose CUI or FCI, there is no subcontractor compliance requirements.
If our company operates in multiple locations, but only two locations have access to CUI, does every location have to be assessed for CMMC compliance?
Only the two locations that have access to CUI need to achieve Level 2 compliance. The remainder can be omitted from the CMMC certification process unless any have access to FCI – in which case a CMMC Level 1 self-assessment and affirmation should be included in the contract application.
How does NIST SP 800-171 r2 (required for CMMC Level 2 certification) differ from the HIPAA Security Rule?
Not a lot. Many of the differences are subtle (i.e., employees should be trained on recognizing insider threats as part of their security and awareness training) except where NIST families exist that do not appear in the Security Rule (i.e., Personnel Security). However, although it has been suggested that NIST SP 800-171 r2 can be used to assess compliance with the Security Rule, this can depend on how Covered Entities and Business Associates have applied the addressable implication specifications of the Administrative, Physical, and Technical Safeguards.
ComplianceHome is a registered trademark. Copyright © 2025 ComplianceHome. All rights reserved.